Find information:
Scientists Develop a Software-based Method to Prevent Newly Raised Practical Threats against Mobile Devices and Cloud Platforms
Date:2019-12-03
Recently, some kinds of practical attacks are developed by hackers to steal information in mobile devices and cloud platforms. The typical attacks are board-level physical attacks and memory-based side-channel attacks. They only require low-cost attack tools and can be easily leveraged by underground industry to perform criminal activities.
Existing methods to prevent the newly raised attacks are by integrating specialized security hardware into the CPU, which require re-designing the CPU hardware, such as the Intel SGX, AMD SEV, Sanctum and Komodo technologies (Fig.1). However, how to prevent these attacks for off-the-shelf devices, especially for ARM devices who dominate mobile markets and have increasing momentum in cloud markets but are not equipped with any security mechanisms to prevent such attacks?
Associate professor ZHAO Shijun at Institute of Software, Chinese Academy of Sciences designs a new secure enclave architecture called SecTEE to prevent these attacks for ARM devices. The related research entitled “SecTEE: A Software-based Approach to Secure Enclave Architecture Using TEE” was presented and published in the 26th ACM Conference on Computer and Communications Security, one of the Top4 conferences in the information security field.
The proposed method (Fig.2) only requires a small memory chip called on-chip memory (OCM), which is a common block in all chips. SecTEE implements a small kernel running on the OCM, and the kernel takes the OCM as the only working memory and encrypts all the data/code outside the chip, i.e., DRAM to prevent physical attacks. Besides, it leverages the cache coloring mechanism and cache locking mechanism to guarantee that malicious software attackers cannot learn the memory access patterns of trusted applications by manipulating the cache.
SecTEE also provides rich trusted computing features, by which users can attest the security status and identities of the applications, which is a basic security requirement for cloud platforms.
The proposed countermeasure can be applied to all ARM A-series devices, and can also be applied to other devices with a hardware separation mechanism, such as RISC-V devices with MultiZone Security.
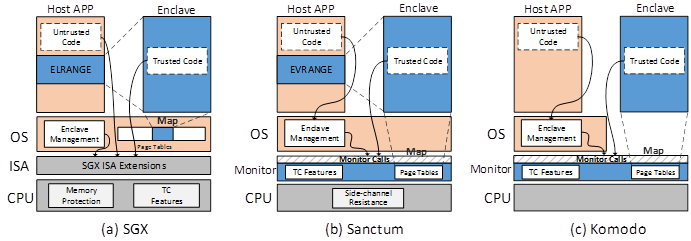
Figure 1. All existing methods requires to modify the CPU hardware. (a) Intel SGX for x86 CPUs. (b). Sanctum for RISC-V CPUs. (c). Komodo requires hardware memory encryption engine which does not exist on ARM CPUs. (Image by Shijun Zhao)
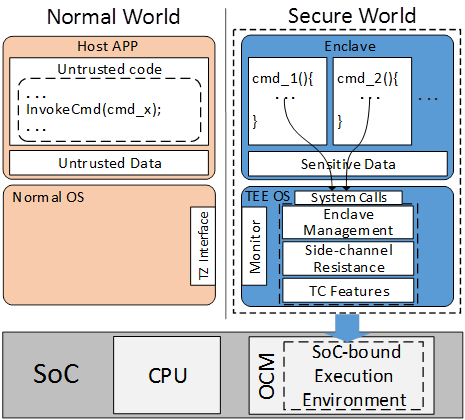
Figure 2. The architecture of SecTEE. (Image by Shijun Zhao)
